The Ultimate Cheat Sheet To Being Anonymous On Internet.

Hello dear hackers welcome back to my another blog, hope you all are good, happy and enjoying your life.
So in this blog, I’m going to discuss about internet anonymity & privacy and going to give you complete guidance about it.
In this blog you will learn, how to be a completely anonymous on internet.
We will also discuss about following things. ☟
- How to hide your real identity.
- What is TOR browser.
- How to perform hacking tasks to being completly anonymous.
- How to use proxychain.
- How to get your anonymity one step ahead.
- How to use specific operating system, which keeps you anonymous on internet.
Before start writing the blog, I have such a small request to all of you, I always right articles on cyber security, ethical hacking, penetration testing. So if you didn’t follow, then follow me first and clap on this article, because that’s give me a motivation to write something new !!
If you didn’t follow me on my socials, here it is.
☛ My-Twitter
☛ My-Linkedin
☛ My-GitHub
Thank you !!!
Let’s Start !!!
1) Tor Browser :

Tor browser is especially developed for access the internet anonymously.
Tor Browser isolates each website you visit so third-party trackers and ads can’t follow you. Any cookies automatically clear when you’re done browsing. So will your browsing history.
Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.
Your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays.
☛ Download
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
2) DuckDuckGo Search Engine:

DuckDuckGo is the internet privacy company for everyone who’s had enough of hidden online tracking and wants to take back their privacy now.
Read the privacy policy of duckduckgo to understand better.
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
3) ProxyChain :

PorxyChain is a tool where you can redirect your internet traffic through a multiple proxy servers.
Before know more about proxychain, first of all we need to know,
What is proxy server ?
A proxy server is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network.
There are 3 types of proxy servers.
- Socks Proxy Server : This type of proxy server provides a connection to a particular server.
- HTTP Proxy Server : This proxy was developed to process a one-way request to the web pages using HTTP protocols
- SSL Proxy Server : This type of server was developed using the concept of TCP relaying being used in the SOCKS proxy protocol to allow Web Pages’ requests.
✯ How To Use Proxy Chain ✯
First of all you need to install TOR SERVICE, using command.
sudo apt-get install tor☟ To use ProxyChain, follow these methods. ☟
Jump on your terminal and type
sudo nano /etc/proxychain.confWhen you open the proxychain configuration file, it will look like this ☟
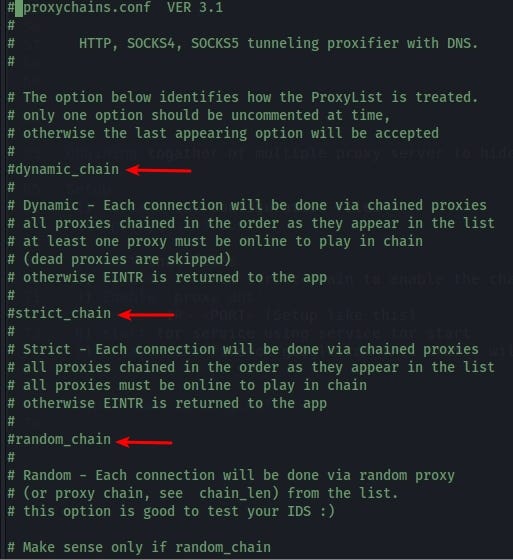
As you can see 3 types of chain
- Dynamic chain
- Strict chain
- Random chain
Remove just one ‘#’ from chain, to enable the chaining rule, I’m recommend you to use, either strict chain (if you’re proxy is live anytime) or you can use dynamic chain (If your proxy are not live anytime.)

Must enable ‘proxy_dns’, as you can see above “Example” tab, how to setup proxy server.
ProxyType <IP> <PORT> <USER> <PASSWORD>
socks5 192.168.67.78 1080 lamer secret
# ProxyType = socks5
# IP = 192.168.67.78
# PORT = 1080
# USER = lamer
# PASSWORD = secretHere you can understand proxy setup format , setup your proxy under 2nd red rectangle as shown in image.
I setup my proxies as you can see here.

But I don’t start, shows red arrow proxy, because it’s directly connect you to tor.

You will see, my proxy is dead but according to dynamic chain, one proxy is dead it will automatically connet to next proxy.

But, If you enable default socks4 TOR proxy.

and start your tor service, THEN….

As you can see, Tor is also connected with given proxy and your ProxyChain will start and run with your TOR services.
Here I shown you demo via screenshots that how to use ProxyChain and ProxyChain with TOR.
☟ Here are some resourses for best ever proxies. ☟
☛ FreeProxy
☛ Geonode
☛ Spys
☛ Free-Proxy-List (Best resourses to get free and paid proxies)
☛ Free-Proxy
☛ Webshare (Paid)
☛ Froxy (Paid)
☛ SmartProxy (Paid)
☛ Asocks (Paid)
☛ NetNut (Paid)
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
4) Burner Phone :

A burner phone, or burner, is an inexpensive mobile phone designed for temporary, sometimes anonymous, use, after which it may be discarded.
while buying burner phone keep remind. “There are any type of your identity shouldn’t link with that phone.”
You have to buy burner phone using cash OR if you are gonna order it online then use virtual credit card services.
Burner phones usually come with a prepaid SIM card with credit already loaded into it for you to call or text right away. When the credit is used up, you can either dispose of the phone or load more credit into it.
There are many places where you can get a burner phone, like mobile phone vendors, department stores like Walmart or Target, or MVNO (Mobile Virtual Network Operator) like AT&T and T-Mobile. You can also get one online from sites like eBay or Amazon.
☟ Here are some features of burner phone. ☟
☛ To protect your identity when communicating by phone.
☛ This is totally untraceable phone. Some security researchers claim that, NSA can’t track your phone location.
☛ When online shopping, to avoid spam calls and messages.
☛ To protect your primary phone from accidents.
☛ To hide your communications.
☛ To get a phone cheaply. You can buy these phones just in 10$ to 15$.
☟ Here are some burner phone online sources. ☟
☛ Tracfone is one of the best company who sells burner phones.
☛ Mintmobile
☛ Amazon-link 1
☛ Amazon-link 2
☟ Use following keywords to find and get burner phone. ☟
☛ Prepaid flip phone at&t
☛ Prepaid flip phone tmobile
☛ Prepaid flip phone tmobile locked
☛ Prepaid flip phone At&t locked
☟ Here Some bonus tips to use burner phone ☟
☛ The difference is that a locked phone has a software code on it that, “prevents you from using it on another network.” An unlocked phone either doesn’t have the software lock on it or someone was able to get a code that unlocks the software.
☛ Always use locked and old type of keypad burner phone, rather than using smart phone, flip phone are the best !!!
☛ If you are not able to get burner phone then you can use burner app into your exesting smart phone. But somewahre it will less secure and you could be trace.
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
5) Kali-Whomi Tool :

Kali whoami-project is most useful tool to enhance your privacy, whicle surfing internet anonymously.
In this tools, 9+ different modules to ensure the highest possible level of anonymity also solves possible problems without disturbing you with the Bug fixer module, which is in development.
Here are some following module which you can change on your system, to enhance your privacy one step ahead.
- Anti mitm (You got ban,during MITM attack)
- Log killer (Distroy log files on your system)
- IP changer (Hide your real IP, and redirect traffic through TOR.)
- Dns change (Change your DNS server provide by ISP)
- Mac changer (Change your MAC address)
- Anti cold boot (Avoid RAM dumping)
- Timezone changer (Change your timezone)
- Hostname changer (Change your hostname)
- Browser anonymization (Configures the browser to be privacy focused)
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
6) Security Based Linux Distro :

In this topic we are going to see about some privacy & anonymity baced operating system which keeps to help you secure, safe and anonymous on internet.
- Tails :
Tails Stands for The Amnesic Incognito Live System.
Tails uses the Tor network to protect your privacy online and help you avoid censorship. Enjoy the Internet like it should be.
☛ Download Tails - Qubes OS :
Qubes OS is a free and open-source, security-oriented operating system for single-user desktop computing.
Qubes OS leverages Xen-based virtualization to allow for the creation and management of isolated compartments called qubes.
☛ Download Qubes - Whonix :
Whonix is a Kicksecure–based security hardened Linux distribution. Its main goals are to provide strong privacy and anonymity on the Internet. The operating system consists of two virtual machines, a “Workstation” and a Tor “Gateway”, running Debian GNU/Linux. All communications are forced through the Tor network.
☛ Download Whonix
Edward Snowden , the person who was the ex employee and subcontractor of National Security Agency of USA.
He admit, that Tails, Qubes & Whonix OS is a most secure OS ever.
Even he used these OS.
If You wants to know more about operating system, then you should read this blog.
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
7) Encrypted email :

You should have encrypted email address for communication to the world.
☛ Protonmail (Best ever email services.)
☛ Fastmail (Best paid email services.)
☛ Tutanota Mail (Alternative of protonmail.)
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
8) Bonus Points :

- Use always TOR + PROXYCHAIN while using internet.
- I recommend you to use paid & live proxies.
- I suggest you to use strict chain in proxychain, because strict chain uses all proxies in the list will be used and chained in the assigned order.
This chain get disconnect when one proxy is dead. - Forget about VPN, if you wants to be a complete anonymous.
- Turn off your cookie settings while you are browsing internet.
- Don’t use any browser extention into your TOR browser.
Use as it is !!! - Physical PC for hacking, it takes you one more step ahead and helps to enhance your anonymity rather than VM. (Virtual machine)
- Use always high speed internet while using proxychain & tor.
Because in this case, your internet traffic goes to across multiple servers and because of this reason, your speed will definetly decrease. Don’t forget to check your DNS Leak Test for confirmation. If it’s not showing your real IP & every refresh shows different IP, that means you are successfully connected to tor.
On these following sites you can check :
☛ DNS-Leaktest
☛ BrowserLeaks
☛ IP-Leak
☛ DNS-Leak-Test
☛ DNS-Leak-Test 2
☛ DNS-Leak
☛ DNS-Check - Anonsurf is a tool to anonymize our complete system traffic tunneling via TOR using IP-Tables. Also You can use these tools which helps you to change you’re IP address frequently in 3 seconds
☛ Tor-IP-Changer
☛ Tornet - Here are some habits, that you needs to change to be a anonymous.
☆ Chrome ➡️ Brave, TOR.
☆ Google ➡️ DuckDuckGo.
☆ Gmail ➡️ Protonmail, Fastmail, Tutanota Mail
☆ Windows ➡️ Linux, Tail, Qubes, Whonix.
☆ Whatsapp ➡️ Signal, Telegram.
☆ Paypal ➡️ Bitcoin.
☛ PrivacyX is the site to get more tools to be a anonymous.
I hope you guys love this blog.
If you like it, then don’t forget to follow, subscribe and claps.
I’ll see you with next article.

