Complete Bug Bounty Recon Fundamentals.

Hello dear hackers, welcome back to my new blog, I hope so you all are good !!
So today, in this blog, we are going to discuss about complete bug bounty recon fundamentals, tips, tricks and all types of techniques.
Recon is the first and most important part of hacking, either it could be pentesting or bug bounty.
If you are perfect in recon process, then you are vulnerability analysis process and exploitation process will be lot more easy.
Before start writing the blog, I have such a small request to all of you, I always right articles on cyber security, ethical hacking, penetration testing. So if you didn’t follow, then follow me first and clap on this article, because that’s give me a motivation to write something new !!
If you didn’t follow me on my socials, here it is.
☛ My-Twitter
☛ My-Linkedin
☛ My-GitHub
Thank you !!!
Let’s Start !!!
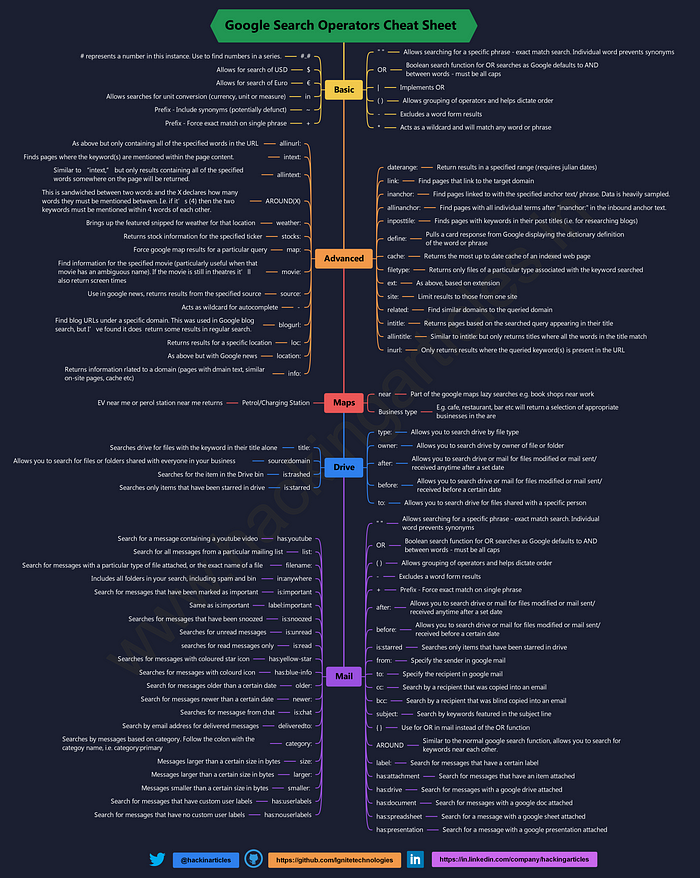
1) Google Dorks :
Google dorks it’s nothing but, it’s google search filters, where you can search particular link, keyword, title or file types of exact particular website.
☟ Let’s check some Google dorks as follows ☟
✦ site:google.com (It will gives you, only “example.com” site result)
✦ intext:“hello man” (It will only showing you TEXT that, you put into intext)
✦ inurl:“admin” (It will only showing you keyword that is inside the URL)
✦ intitle:“password” (It will show you at the title as a main header)
✦ filetype:pdf (It will show you only, particular file type result of particular site)
✦ link:www.google.com (When you use the link keyword followed by the URL, it will show you all the site that link back to the URL specified.)
✦ allintext:“Hello Man” (If you use the allintext keyword, Google will restrict your search to those pages that have ALL of the search terms you specify in the text of the page.)
✦ allinurl:“admin” (If you use the allinurl keyword, Google will restrict your search to those pages that have ALL of the search terms you specify in the URL of the page.)
✦ allintitle:“password” (If you use the allintitle keyword, Google will restrict your search to those pages that have ALL of the search terms you specify in the title of the page.)
✦ info:www.google.com (It will gives you information of given web page)
✦ related:www.google.com (It will gives list web pages that are “similar” to a specified web)
✦ cache:www.google.com (If you include other words in the query, Google will highlight those words within the cached document.)
✦ define:“Hacker” (The query will provide a definition of the words you enter after it, gathered from various online sources.)
✦ before: 2010 (It will show you result of site before 2010)
✦ after: 2010 (It will show you result of site after 2010)
✦ ext:php (Used to find out particular extention of given site)
Here is some google dorks which helps you in bug bounty recon
☟ I’m going to gives you, some additional dorks which will help you for OSINT. ☟
✦ phonebook: “India” (Search phonebook releted query)
✦ maps: “America” (Search particular location)
✦ book: “bug bounty bootcamp” (Search particular books)
✦ movie:Avengers (Search particular movies)
✦ weather:London (Search weather of any particular city)
☟ Some operator to use in google dorks.☟
⇾ * (Means wildcard character, that means DISPLAY EVERYTHING)
⇾ “ ” (Means quotation mark, that means DISPLAY EXACT KEYWORD, it only use for intext, inurl, intitle,defile dorks OR use for search any strings type of keyword)
⇾ | (Means PIPE Symbol, which is use for “either this or that” type of statement, let me explain with following dork example)
inurl: “admin” | inurl: “login” (you can also write, inurl: “admin” OR inurl: “login”)
As you can see above 2 inurl dorks, in this case, google will try to find out 1st keyword of left side of PIPE, if it got admin keyword the OK!! OTHERWISE it will try 2nd dork, means right side of PIPE and try to find login keyword
⇾ AND (It return result with all given keywords.)
“USA” AND “China” (It will gives result of both keywords.)
⇾ intex/inurl/intitle (It searches for term designated area.)
You can also use “ — ”symbol to exclude any result in google dorks, you can say this minus sign OR dash OR hyphen
For Exmaple, site:google.com intext: “programming” -inurl:HTML
In this example, you can see intext programming but you can’t see inurl
HTML as a result
These are all Google search filter keyword where you can find database what you want !!
☟ Some google dorks resourses for bug bounty hunting. ☟
✦ Google Hacking Database (GHDB) - Exploit-DB
✦ Google Hacking - Free Google Dorks for Recon
✦ Google Dorks Bug Bounty OR use Live-Tool By Mike Takahashi
✦ Useful Google Dorks For WebSecurity And Bug Bounty 1
✦ Useful Google Dorks For WebSecurity And Bug Bounty 2
✦ Google Dork File Finder
✦ DorkSearch
✦ Bug Bounty Helper
✦ BigBountyRecon
✦ Bug Bounty Dorks (Hunt for programs varying from Private VDP Programs.)
☟ This is complete google dorks cheat sheet. ☟
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
2) SSL Enumeration :
SSL enumeration, is the enumeration where you are gatharing the information about SSL certificate of that perticular web application.
There are lots of tricks and technique to gather information about it.
Let’s check one by one as follow !!
✯ SSL Enumeration Using Nmap ✯
☛ Script ssl-cert☛ Script ssl-cert-intaddr☛ Script ssl-date☛ Script ssl-dh-params☛ Script ssl-enum-ciphers☛ Script ssl-heartbleed☛ Script ssl-known-key☛ Script ssl-poodle
✯ SSL Scanning Tools ✯
☛ Sslscan
☛ S3scanner
☛ Sslyze
☛ TLSSLed
☛ Sslh
☛ SSL.Com
☛ SSL.Org
☛ SSLShopper
☛ SSLCchecker
☛ Godaddy-SSl-Check
☛ Decoder-SSLChecker
☛ CertificateDetails
✯ Online SSl Scanner ✯
☛ ssllabs
☛ SSL Tools
☛ SSL/TLS Scanner
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
3) CMS Enumeration :
A Content Management System (CMS) is an application that is used to manage content, allowing multiple contributors to create, edit and publish.
Using following tools you can gather information about CMS
☛ cmseek
☛ joomscan
☛ wpscan
✯ Online CMS Scanning Tools ✯
☛ What CMS
☛ CMS Detector
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
4) DNS Enumeration :
DNS enumeration is the process of locating all the DNS servers and their corresponding records for an organization. A company may have both internal and external DNS servers that can yield information such as usernames, computer names, and IP addresses of potential target systems
✯ DNS Enumeration Using Nmap ✯
☛ Script dns-blacklist☛ Script dns-brute☛ Script dns-nsec-enum☛ Script dns-srv-enum☛ Script dns-zone-transfer☛ Script dns-nsid☛ Script dns-fuzz☛ Script dns-check-zone
✯ DNS Scanning Tools ✯
☛ dig
☛ Nslookup
☛ BIND9
☛ Dnsrecon
☛ Dnsenum
☛ Dnstwist
☛ Dnsx
☛ DnsProbe
☛ Fierce
☛ GoogleDNS
☛ Google-Toolbox
☛ msdnsscan
☛ Raccoon
☛ host
☛ whois
✯ Online DNS Scanner ✯
☛ DnsDumpster
☛ Netcraft
☛ ICANN Lookup
☛ Domain Tools
☛ Robtex
☛ DNSlytics
☛ CentralOps
☛ Whois
☛ Who.Is
☛ WhoisxmlAPI
☛ MXtoolBox
☛ WhoisFreaks
☛ BigDomainData
☛ Whoxy
☛ MyIP.ms
☛ Dmitry (Multipurpose tool used to DNS Lookup, IP Lookup, Gather Netcraft info, Port Scanning and many more)
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
5) Technology Enumeration :
Technology enumeration is the process where you can find about technology, webserver, operating system, web hosting, CMS, CDN, Programming language, behind the websites
✯ There are some tools to find out the web technology enumeration ✯
☛ Wappalyzer
☛ BuiltWith
☛ WhatWeb
☛ Netcraft
☛ Retire.js
☛ NerdyData (Chrome-Extension)
☛ httpx-toolkit
☛ Nuclei (One of the most powerfull and ultimate tool for multipurpose web activity)
Wappalyzer, BuiltWith are the useful extention for hackers.
I already written the blog on hackers extention, if you don’t read that blog then this is the link. ☟
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
6) WAF Enumeration :
WAF stands for Web Application Firewall
I’ts the process of enumeration, where you can detect the firewall which is running behind the website.
✯ There are some tools and some nmap scripts to enumerate web application firewall. ✯
☛ Wafw00f
☛ Script http-waf-detect☛ Script http-waf-fingerprint☛ Script firewall-bypass
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
7) Port Discovery :
A port discovery or port scanning is a common technique, where hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out whether they are receiving or sending data. It can also reveal whether active security devices like firewalls are being used by an organization.
When hackers send a message to a port, the response they receive determines whether the port is being used and if there are any potential weaknesses that could be exploited.
✯ There are some tools to use for port discovery. ✯
☛ Nmap
☛ Masscan
☛ RustScan
☛ Naabu
☛ NimScan
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
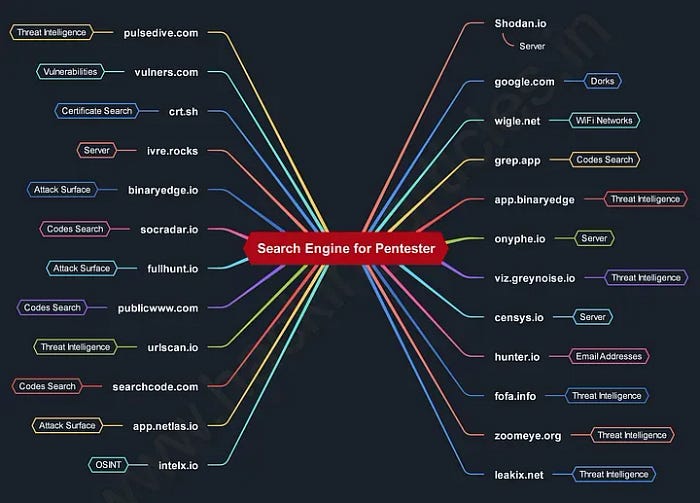
8) Online Hacker Search Engine :
Online hacker search engine is a platform, where you can search all various types of servers connected to the internet using a variety of filters. Some have also described it as a search engine of service banners, which are metadata that the server sends back to the client.
✯ There are some search engines, to get information passively for bug bounty ✯
☛ Shodan (Python library for terminal)
☛ Censys (Python library for terminal)
☛ Hunter
☛ Zoomeye
☛ GrayNoice
☛ Uncover
☛ Netlas
☛ CriminalIP
☛ PublicWWW
☛ HunterHow
☛ Quake
☛ ReconDog
☟ Category wise hacker search engine list ☟

⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
9) Web Crawling :
What is web crawling? Web crawling is the process of indexing data on web pages by using a program or automated script.
These automated scripts or programs are known by multiple names, including web crawler, spider, spider bot, and often shortened to crawler.
Basically web crawler find out the hidden endpoints of website.
✯ There are some tools for web crawling and parameter endpoint searching ✯
☛ Arjun
☛ LinkFinder
☛ SecretFinder
☛ Gospider
☛ Paramspider
☛ Hakrawler
☛ Meg
☛ Crawley
☛ X8
☛ Getallurls
☛ SpiderSuite
☛ Katana
☛ GAU
☛ URO
☛ URLdedupe
☛ CommonCrawl
☛ WayMore
☛ WayBackurls
☛ Photon
✯Here are some tools to crawl, copy / clone and take the screenshot of websites.✯
☛ Eyewitness
☛ Gowitness
☛ Aquatone
☛ Httrack
☛ Pikwy
☛ SurfOffline
☛ SoftbyteLabs
☛ Tensons
☛ Metaproducts
☛ Spadixbd
✯ Here are some tools which are used to moitoring websites.✯
☛ Visualping
☛ FollowThatPage
☛ Page2RSS
☛ WatchThatPage
☛ Update-Scanner
☛ URLscan
☛ Check4Change
☛ Anew
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
10) GitHub Reconnaissance :
Github recon is the process, where you can gather the information from github which is intentionally or unintentionally exposed by web developer.
In github recon, you can find sensetive data such as API key, private PGP key, usernames, passwords, email address, logs etc.
✯ There are some following tools useful for git recon ✯
☛ Trufflehog
☛ GitHub-Dorks
☛ GitGot
☛ Git-Monitor
☛ Gitrob
☛ Git-hound
☛ Gittyleaks
☛ Git-secrets
☛ Watchtower
☛ Octosuite
☛ Gitrecon
☛ GitStalk
☟ GitHub recon dork list ☟

⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
11) Fuzzing & Content Discovery :
According to OWASP definition, Fuzzing is the art of automatic bug finding, and it’s role is to find software implementation faults, and identify them if possible.
In content discovery, content can be different types such as images, files, videos, and so on. There are 3 main ways to discover content on web pages which are: Manually, Automated, OSINT (Open-Source Intelligence) methods.
✯ There are following tools useful for fuzzing and content discovery ✯
☛ Dirb
☛ Dirbuster
☛ Gobuster
☛ Dirsearch
☛ Wfuzz
☛ FFUF
☛ Feroxbuster
☛ Kiterunner
✯ Some payload resourses ✯
☛ SecLists
☛ Wordlists
☛ PayloadsAllTheThings
☛ Fuzzdb
☛ PayloadBox
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
12) Subdomain Enumeration :
Subdomain enumeration is the process of finding sub-domains for one or more domains. It helps to broader the attack surface, find hidden applications, and forgotten subdomains.
✯ There are two types of subdomain enumeration techniques ✯
✪ Active subdomain enumeration
✪ Passive subdomain enumeration
Let’s check one by one
✪ Active subdomain enumeration :
There are some types of active subdomain enumeration as follows
➾ Brute Force Enumeration (ffuf, wfuzz, dirbuster)
➾ Zone Transfer (nslookup, dig, dnsrecon tool)
➾ DNS Records (A, AAAA, MX, TXT, CNAME, NS Records using dnsrecon tool)
✪ Passive subdomain enumeration :
There are some types of passive subdomain enumeration as follows
➾ Tools
➾ Certificate Transparency [crt.sh] OR [Github-Repo] OR [NSE Script]
➾ Google Dorking (we discussed about it !!)
✯ There are some tools to get subdomain passively ✯
☛ Knockpy
☛ Sublist3r
☛ Turbolist3r
☛ Subfinder
☛ Assetfinder
☛ Amass
☛ Findomain
☛ Subbrute
☛ Chaos
These are some tools to get sobdomain
Here we are finishing the Bug Bounty Recon Fundamentals !!
Let’s Discuss About Some Bonus Tips
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
✯ BONUS TIPS ✯

☛ Bug hunting getting lot more easy, it depends upon your recon, if you do deep recon, then there are lots of chances increases to got bug.
☛ Most of the times we need, a tools with multiple functionality such as Checker tools, Text tools, Converter tools, Generator tools, Developer tools and so many things but don’t worry, I got solution ViewDNS is online web site including over 350+ quick & easy to use web tools.
You must check it out, I promise you will never disappoint.
☛ Store every historical data, that you find from different sources including your recon data, all subdomains, your exploits, payloads and everything that you gather.
☛ Keep updated the given hacking tools regularly on your attacker machine.
☛ Keep learning new things and don’t forget to update and grow your knowledge.
☛ Make cheat sheet of payload OR make it always ready to your PC
above I just give payload resources. Check it out !!
☛ Learn from your mistakes, it will make you perfet !!
☛ Read articles, blogs, published reports on cyber security and bug bounty daily.
https://md5decrypt.net/en/Conversion-tools/
☛ Make checklist of url and vulnerabilities. If you want to perform it better then use note keeping sofware as follows
➾ Evernote
➾ Notion
➾ Cherrytree
➾ This & This checklist you should never miss !!!
➾ This is most useful source for you !!!
MagicRecon don’t forget to use this !!!
☛ Write a proper bug bounty report after found a bug.
If you don’t know, how to write a bug bounty report, then this is the link
go and check it out ☟
☛ The “Chaos” is most beautiful project discovery platform.
If you boared with hackerone and bugcrowd then try it.
GitHub-Repo-Of-Chaos (as I already mention above this tool is also useful for finding subdomain.)
☛ Use all “tomnomnom-github-tools” for bug bounty, i’ts such a useful tools
☛ “reNgine” is an automated reconnaissance framework for web applications with a focus on highly configurable streamlined recon process via engines.
Use reNgine tool, if you are master in manual recon
☛ RreconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform scanning and finding out vulnerabilities
☛ “Nuclei” is a most populer YAML templete based, web vulnerability scanner which you must use, while recon or exploiting.
This is the guide to use nuclei tool
➾ The Ultimate Guide to Finding Bugs With Nuclei
☛ “Ciphey” tool, which is fully automated decryption/decoding/cracking tool using natural language processing & artificial intelligence, along with some common sense.
☛ You should understand website structure that, how website build and other. So you have to copy the website in your local machine.
“Httrack” is an offline browser utility, allowing you to download a World Wide website from the Internet to a local directory, building recursively all directories, getting html, images, and other files from the server to your computer.
☛ “CyberChef” the cyber swiss army knife — a web app for encryption, encoding, compression and data analysis.
☛ Conversion-tools is the good tool for you to detect automatic hashes and decode them !!!
☛ “Nmmapper” offloading cybersecurity defense tools from nmap to subdomain finder, theHarvester
☛ “Waybackurl” is most popular and powerfull tool ever, and your best friend as well which you can get multiple vulnerable endpoint parameter and vulnerable URLs.
Don’t forget to check it out
⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚⮘⮚
I hope you guys enjoy the blog.
If you like it, then don’t forget to follow, subscribe and claps.
I’ll see you with next article.

